Executive Summary
Since the first block of bitcoin was mined in January 2009, cryptocurrency has transformed from an obscure, experimental corner of the market to an increasingly popular investment option trying to become mainstream. Famous for its dramatic highs and infamous for its subsequent lows, cryptocurrency has fascinated many as a fast-moving corner of the market... capturing both media and more and more consumer attention, to the point that many advisors who may have once dismissed cryptocurrency as a legitimate investment option are being asked to reconsider it by a growing number of clients ready to take on at last a little risk. In fact, a recent FPA Trends In Investing survey found that one in four advisors have indicated that they have considered adding cryptocurrency to client portfolios—a massive increase from what was historically fewer than 2% of advisors interested. However, in order for advisors to have confidence in cryptocurrency as a sound client portfolio option, it is important to know how to do more than trade cryptocurrency; advisors must also understand how to securely store it.
Because while cryptocurrencies like Bitcoin solve many unique technological challenges that have made entirely digital currencies infeasible before, cryptocurrency is not held in traditional brokerage accounts like stocks, bonds, mutual funds, and ETFs, which presents unique challenges for securely storing cryptocurrency. In addition, unlike funds that are transferred via ACH and can be retrieved in the event that they were accidentally transferred between the wrong accounts, there is no central authority that can 'undo' an accidental cryptocurrency transaction. Instead, cryptocurrency is traded using public and private keys, which allow cryptocurrencies to be received and spent, respectively. While public ‘receiving’ keys can be used, generated, and distributed on a case-by-case basis without any personal risk, private ‘sending’ keys need to be securely guarded. If someone is trading in large amounts of cryptocurrencies, then the risk is even higher, and the keys will need to be safely stored in what is referred to as a (digital crypto) ‘wallet’. Yet at the same time, a key challenge with cryptocurrency storage is that the sophistication of the storage strategy used needs to also match the technical sophistication of the investor, as there’s a genuine risk of losing funds (or more specifically, permanently losing access to one's own cryptocurrency holdings) in the event that someone doesn’t quite know what they are doing.
So what is a safe option, then, for cryptocurrency storage? There are a wide range of storage options. In theory, one of the most secure methods possible is what’s known as a ‘paper wallet’- which refers to a wallet generated fully offline and stored in a physical format. However, the challenges of actually generating a paper wallet fully offline, and some technical aspects of how Bitcoin transactions actually work, make paper wallets a poor choice for most users. At the same time, despite the ease of use available from some wallets that can be installed on a computer, storing keys on a computer that has ever been connected to the internet is also a bad idea since an internet-connected computer can be compromised (and if that computer is the gateway to thieves permanently stealing one's sizable cryptocurrency holding, it is best to assume that any such computer has already been compromised!?).
Thankfully, there are two general cryptocurrency solutions advisors can give to their clients (or use) themselves. For the less tech-savvy advisor, using a reputable exchange or storage provider is emerging as a lower-risk solution—particularly as more mature firms are developing in this space. Such storage violates an ‘old’ cryptocurrency adage of “not your keys, not your coins,” since it is true that the service provider does have the owner's keys for (and therefore ultimate control of) the cryptocurrency funds, but for someone who otherwise would have limited ability to secure their funds, this may still be a better alternative, particularly if features such as 48-hour waiting periods are added before transactions can be made. However, for the slightly more tech-savvy user, hardware wallets are likely the ideal balance between security and the technical sophistication needed to implement a strategy. Hardware wallets are single-purpose computing devices that are designed solely to store cryptocurrency keys. The single-purpose nature of hardware wallets means that they can be used without fear of being compromised, even if a user is interacting with the wallet through a compromised computer. While there are some basic standards that users would want to ensure a hardware wallet meets, quality hardware wallets use a combination of security features that help ensure that someone’s coins are safe and retrievable even in the event that their hardware wallet is lost or stolen.
At the end of the day, cryptocurrency is likely here to stay, and consequently will only receive more attention in the future. As a result, if someone is going to own cryptocurrency, appropriate security measures need to be taken to address the unique nature of how these assets are owned and held. Importantly, though, as the amount invested grows, so too does the need to safeguard those investments. This is especially true for those who are looking to invest not only for themselves, but also for others. But the good news is that ultimately, with a little bit of research, advisors can find a secure storage option that opens up an entirely new side of investing for their clients (and even themselves if they are so inclined)!
As cryptocurrencies become increasingly mainstream, financial advisors may be facing more clients asking about or looking into solutions for purchasing their own cryptocurrency. Unlike other types of investment assets (e.g., stocks, bonds, mutual funds, and ETFs) that can generally be held with third-party custodians (usually with little concern), cryptocurrency has unique characteristics that can make identifying secure storage methods less straightforward.
Furthermore, unlike the earliest cryptocurrency adopters who tended to be more tech savvy and were more likely to be comfortable navigating the challenges regarding the secure storage of their cryptocurrency on their own, new entrants to this market may lack that same level of sophistication and may need to consider different solutions for storing their investment.

Nerd Note:
While there are a number of different cryptocurrencies with their own nuances, since Bitcoin has historically been and remains the dominant cryptocurrency, this post is written with Bitcoin in mind. That said, many of the same principles covered translate to other cryptocurrencies as well.
Why Cryptocurrency Is Different From Other Types Of Assets
Cryptocurrency is a type of digital asset that uses the study of writing and solving codes, known as cryptography (hence, “crypto”-currency) to secure transactions and allows users to engage in exchange without needing to rely on any centralized authority. While there are many potential use cases of cryptocurrency—from mundane instances of microtransactions and more efficient international exchange, to more controversial objectives such as protecting one’s wealth from predatory governments—the reality is that the innovation that came from the development of the ‘blockchain’ (explained later) is significant, and cryptocurrencies are likely here to stay.
In his book, Mastering Bitcoin, Andreas Antonopoulos describes the three major challenges of developing a viable digital currency:
Three basic questions for anyone accepting digital money are:
- Can I trust that the money is authentic and not counterfeit?
- Can I trust that the digital money can only be spent once (known as the “double-spend” problem)?
- Can I be sure that no one else can claim this money belongs to them and not me?
While these challenges are not unique to digital currency – current financial systems and institutions have developed their own ways to address these problems with other forms of currency – these challenges were particularly significant in the context of developing an entirely digital form of currency.
Advancements in cryptography were the key to solving this problem. Early attempts at building digital currencies were centralized (i.e., owned or managed by a central authority) and therefore significantly prone to attack. For instance, a group of hackers, or even a government itself, may view a cryptocurrency as violating existing laws or their own vested interest in a financial institution, and could easily attack the centralized service to render it useless. Alternatively, a corrupt centralized authority could engage in wrongdoing of their own by creating a cryptocurrency designed to steal from their users.
Bitcoin – conceptually created via the publishing of a 2008 paper by a pseudonymous author called Satoshi Nakamoto, and then implemented via a network also created by Nakamoto in 2009 – was revolutionary in how it used cryptography to create a decentralized system not owned or controlled by any one individual or organization. Instead, control of the system is ‘decentralized’ to computers all around the world that are jointly participating to maintain the security of the network.
Because of this decentralization, Bitcoin is not prone to attack in the same way as centralized systems and allows users to (a) trust that currency is authentic, (b) trust that currency cannot be spent more than once, and (c) trust that no one else can claim the money that they owned.






Nerd Note:
The technical challenge that Nakamoto overcame was developing a novel solution to a complex mathematical problem known as the “Byzantine Generals’ Problem.” Antonopoulos describes this as:
Briefly, the problem consists of trying to agree on a course of action or the state of a system by exchanging information over an unreliable and potentially compromised network. Satoshi Nakamoto’s solution, which uses the concept of Proof-of-Work to achieve consensus without a central trusted authority, represents a breakthrough in distributed computing and has wide applicability beyond currency. It can be used to achieve consensus on decentralized networks to prove the fairness of elections, lotteries, asset registries, digital notarization, and more.
Public Keys, Addresses, And Private Keys
Keys are the “key” to how Bitcoin works. There are two different types of keys: public keys and private keys. Whereas a public key is like an address you would use to receive funds, a private key is akin to a password you would need to use to send funds.
Cryptocurrency Public Keys And Addresses
You can think of a public key as similar to an email address. Bitcoin public keys are long strings of letters or numbers that begin with either a 1 or a 3. For instance, a public key may look like this:
1NRHSyXMvMq8ZsP8BKAQLSmfZ7HUHXpFYG
Additionally, because the public key above is hard for humans to type, often Bitcoin addresses are shared via QR codes like this:








Nerd Note:
There is a technical distinction between a Bitcoin address (shown above) and a public key. The address is a hashed (i.e., encrypted) version of the public key, but since this is just a mathematical process, we’ll keep things simpler by referring to public keys and addresses synonymously. The hash function currently used by the Bitcoin network allows for 2160 Bitcoin addresses. To put that in perspective, there are roughly 263 grains of sand on all of the beaches on earth. So, there’s little risk of running out of addresses, but even if that became a problem, the network could adopt an alternative hash function.
Despite addresses looking very unfriendly, they are actually quite easy to use since Bitcoin “wallets”—which can really be thought of as a collection of public and private keys (more on both private keys and wallets later) – can greatly simplify the process for the end user.
In practice, if you want to get paid by someone in Bitcoin, you can open up a wallet, the wallet will generate a public key (if you don’t have one already) to serve as a receiving address, and then someone can send Bitcoin to that address in a manner very similar to how they might send an email to your email address.
Notably, the ability to generate public keys 'on demand' means you can also have many different keys that are all directing funds to a single wallet. In fact, many wallets will generate new keys for each transaction for privacy reasons.
Public keys are completely fine to share. You don’t have to worry about someone knowing your public key, because all they can do is send Bitcoin to that address.
Once someone has sent funds to a given public key, the transaction gets recorded in the Bitcoin network “ledger”. The ledger is maintained by Bitcoin “miners” (i.e., individuals operating computers that maintain the security of the Bitcoin network) who are essentially solving complex math problems as part of a process that helps verify the transaction history in the ledger. Roughly every 10 minutes, miners add another “block” of transactions to the ledger, and this series of blocks forms what is known as the “blockchain”.
The blockchain is entirely public. You can go explore the blockchain yourself, which includes all of the addresses that have been used within the Bitcoin network. Again, this public aspect of all Bitcoin transactions (or the blockchain ledger in general) that shows where the cryptocurrency moved to (via public keys) is an essential part of how cryptocurrency solves for the authenticity, no-double-spend, verified-ownership structure without a centralized authority.
However, as was mentioned previously, there are both public and private keys. What you absolutely do need to protect is private keys. Anyone who knows a Bitcoin private key has complete control over those funds.
Bitcoin (and other Crypto) Private Keys
Unlike public keys that only receive money, private keys are used for sending money, and consist of 256-bit numbers. To understand what that means, consider 4-bit numbers (i.e., a number that consists of 4 digits) expressed in binary (i.e., the only numbers that can be used are limited to 0 and 1), such as 0001 or 0111. So, a 256-bit binary number would be a 256-digit combination of 0s and 1s.
Binary numbers can be converted into decimal numbers (i.e., numbers expressed in base 10, which makes use of integers ranging from 0 to 9 and, therefore, results in shorter expression of the same number) or hexadecimal numbers (i.e., numbers expressed in base 16, which uses a system of 16 symbols generally consisting of numbers and letters and therefore results in even shorter expressions yet).
For instance, the same private key may look like the following when expressed as binary, decimal, or hexadecimal:
Binary: 1110111100100011010110101010110011111001000011011001111101001010101011011101100011001001001011100100101100100101011000101110000111011001111010111001011111110000110111111001101110100011101101010000100000100101100001110011100111001011000000010011110110110010
Decimal: 108165236279178312660610114131826512483935470542850824183737259708197206310322
Hexadecimal: ef235aacf90d9f4aadd8c92e4b2562e1d9eb97f0df9ba3b508258739cb013db2
The key point here is just that each of the numbers above are the same, and hexadecimal, because it can accommodate a significantly shorter string of symbols (it just literally doesn't take up as much space to write out), is the most common format for expressing private keys.
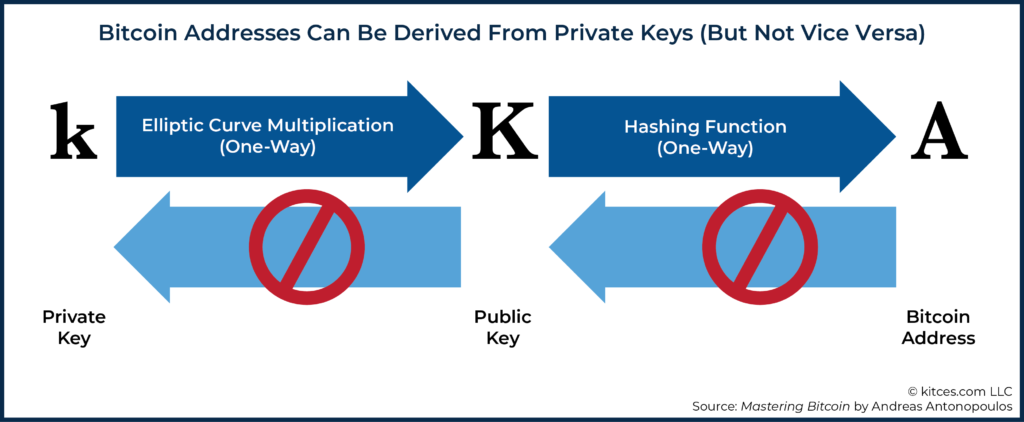
One important thing to note with Bitcoin is that if you have a private key, you can also generate the corresponding public key from that information. For that reason, it is very important to ensure that private keys were generated in a secure manner, as anyone with a private key effectively has the account (public key) and password (private key) needed to move funds.
In fact, although wallets are a common method for creating private keys (and public keys, as noted earlier), someone can actually create a private key entirely themselves. An extra secure way to do this (to ensure no computer anywhere has secretly logged any information about a key) is by following a process such as personally flipping a coin 256 times and recording the result in binary (e.g., 1 for heads; 0 for tails).
Once a private key has been generated, a complex mathematical process called elliptic curve multiplication can be used to determine the public key, and then that public key can be put through a hashing (encrypting) function to arrive at the Bitcoin address. It is important to note, however, that this process does not work in reverse, which is why it’s okay to share a Bitcoin address publicly. In other words, you can use a Bitcoin private key to derive a Bitcoin public key address, but you cannot use a Bitcoin public key address to derive a private key.
The key point with private keys is that they need to be truly random. If private keys are truly random, then there’s effectively zero risk that two people will select the same private key (given that there are more private key combinations than there are grains of sand in the world). However, if you tried to use a private key that could easily be guessed by another person (say, 255 0s followed by a 1), then it is just a matter of time before someone else runs off with your funds.
Similarly, methods exist for generating non-random private keys based on short words or phrases chosen by the user that are run through an algorithm to produce a 256-bit private key (keys such as these are commonly referred to as “brainwallets”), but, again, any process such as this eliminates randomness, which could lead someone else to generating the same private key. Therefore, users who rely on these methods have to be very careful when choosing the words or phrases on which their keys are based.
Bitcoin users should also be careful to opt for Cryptographically Secure Pseudo Random Number Generators (CSPRNGs) when choosing which ‘random’ number generator to use. CSPRINGs include ‘seeds’ that are based on some additional form of ‘randomness’ (e.g., a user moving a mouse around a screen) or other forms of entropy (i.e., uncertain and/or unpredictable inputs that provide greater confidence of randomness). But the fact that they start with seed numbers creates the risk that others starting with the same seed number could end out with the same private key, creating a conflict with another person who would be trying to hold cryptocurrency with the same private key.
In short, it’s important that private keys are generated in a truly secure way, because if they aren’t, then you cannot trust that funds are secure.
Cryptocurrency Wallets
Cryptocurrency wallets provide a convenient way for Bitcoin users to manage their public and private keys. As mentioned previously, many wallets will generate new addresses for each transaction for security purposes, so following that same process with manually generated public and private keys would quickly become overwhelming.
There are a number of different wallet types. While Antonopoulos classifies wallets into the categories below, most wallets have some degree of overlapping cross-over between categories:
- Desktop wallet – A wallet run through a desktop computer. This can be a convenient option with a number of valuable features; however, desktop wallets running on Windows or Mac OS (versus, say, some more secure distributions of Linux) should generally not be considered secure – at least so long as a software wallet is not paired with a more secure type of wallet, such as a hardware wallet (described below).
- Mobile wallet – A wallet run through a mobile device. These can be convenient for day-to-day use involving small transactions, but, again, should not be considered a secure source for storing significant amounts of Bitcoin.
- Web wallet – A wallet primarily accessed through a browser. This method can provide convenience, but again should generally not alone be considered secure for storing significant amounts of Bitcoin.
- Hardware wallet – A specialized hardware device designed just for holding Bitcoin. These devices can be considered secure for storing large amounts of Bitcoin. Good hardware wallets can often be thought of as a nice balance between technical complexity and security for many users.
- Paper wallet – Physically printed keys that can be stored via more traditional means of securing physical assets (e.g., a safe deposit box). If the keys are generated in a secure manner (e.g., via an entirely offline process), then paper wallets can be one of the most (if not the most) secure forms of storage. This is often referred to as “cold storage” or a “cold wallet” (in contrast with a “hot wallet” that has been connected to the internet). Nonetheless, due to other limitations of paper wallets, they are generally not advised for most users.
The challenge with cryptocurrency wallets is that, unless a user is just going to be storing some petty amounts of Bitcoin (i.e., amounts they wouldn’t be overly upset losing), the user must be confident that the wallet itself is secure. If a wallet and/or the device accessing the wallet isn’t secure (e.g., suppose a software wallet was designed to be corrupt and secretly shared keys with others, a user’s computer was compromised and the keys generated were being secretly logged and sent to a hacker, etc.), then a user’s funds are likewise not secure. Which matters, because holding significant amounts of Bitcoin means there's a significant amount of money at stake for hackers or other thieves to steal.
In fact, given how common malicious computer software can be when compromised - and the financial interests of hackers to steal large chunks of cryptocurrency at once by gaining access to a holder's private key - it is generally best to assume that any computer that has ever been connected to the internet is compromised (as hackers can even install malicious code that just waits to see if the computer's owner ever creates a Bitcoin wallet in the future... and then grabs the private key at the moment of creation if not done in a fully secure manner). That’s why “cold storage”, via a paper wallet, can be such a secure option.
However, the secondary challenge of managing paper wallets is the risk of losing those wallets (if that physical piece of paper with a too-long-to-remember private key is lost, the cryptocurrency holdings may never be recovered!), and/or managing the complexity of additional steps of security required of physical (versus digital) assets that may be put in place. That is how we wind up with stories about people helplessly losing hundreds of millions of dollars’ worth of Bitcoin.
So there’s an inherent balancing act between what may be optimal from a security standpoint and what may be optimal from the standpoint of ensuring that security doesn’t extend beyond one’s own capabilities to manage that security, and run the risk of securing one’s Bitcoin ‘too well’ to the point that even they cannot retrieve it.
Cyrptocurrency Exchanges
Before we can really get to the practical aspects of securely storing Bitcoin, there is one other aspect of Bitcoin that must be discussed: exchanges.
Unless someone is paid in Bitcoin or mines it themselves (i.e., dedicates computer resources to maintaining the blockchain and gets compensated for doing so), Bitcoin currency will need to be exchanged for some other form of usable currency. In the US, the current dominant exchange for Bitcoin is Coinbase (others include Binance, Kraken, Gemini, etc.).
Like any currency exchange, you give the exchange one type of currency (e.g., U.S. dollars), and they exchange those dollars for the currency you want, such as Bitcoin (less a transaction fee—e.g., 1.49% for transactions from a US bank account on Coinbase).
An important question for Bitcoin users is how much, if any, cryptocurrency they should keep on the exchange. “Not your keys, not your coins” is an ‘old’ adage in the Bitcoin community. In other words, don’t leave your keys in control of an exchange, because if the exchange controls your keys, they ultimately control the fate of your cryptocurrency.
Recall the discussion of private keys above. When cryptocurrency is left on an exchange, the exchange itself possesses and manages the private keys. If an exchange is hacked or engages in illicit activity itself, users are at risk of losing all of their Bitcoin (e.g., the exchange itself could steal the currency, and/or it could be hacked such that hackers then steal the holdings of everyone who had cryptocurrency stored at that exchange).
And unfortunately, there are plenty of cases of wrongful activity within the history of cryptocurrency exchanges. For instance, Mt. Gox was a Bitcoin exchange based out of Japan and was at one point handling as much as 70% of all Bitcoin transactions worldwide. Then, in February of 2014, Mt. Gox suddenly shut down and filed for bankruptcy, announcing that 850,000 Bitcoins were likely stolen ($450 million worth of Bitcoin at the time; over $53 billion worth of Bitcoin at its all-time high).
Many people who would have otherwise been quite wealthy today saw all their wealth suddenly disappear because, well, “not your keys, not your coins”.
This is why it is generally considered risky to keep Bitcoin stored on an exchange. However, the rise of more reputable exchanges (e.g., now-publicly-traded Coinbase in the US) will continue to complicate this adage.
At the time of writing this post, Coinbase reports the following security precautions:
- 98% of customer funds are stored offline;
- Sensitive data is disconnected from the internet entirely;
- Sensitive data is split with redundancy (basically, no one person single-handedly has access to all the data that would be needed to steal a user's cryptocurrency); and
- Drives and paper backups are distributed in geographically diverse safe deposit boxes and vaults around the world.
Furthermore, Coinbase requires the use of good security practices such as two-factor authentication and even maintains an active “Bug Bounty” program that pays hackers who are able to find and report vulnerabilities within their systems.
Coinbase Exchange
Even though the use of Coinbase to store funds violates the “not your keys, not your coins” adage, depending on the technical sophistication of a given individual, Coinbase’s greater skill and expertise in securely storing funds will, for some individuals, actually be a more secure option than trying (and risk failing) to secure funds on one's own through a hardware or paper wallet.
It is also worth noting that Coinbase does offer varying levels of protection for storing funds on the exchange.
For instance, Coinbase has a “Vault” option that adds extra levels of security, such as a 48-hour time delay on transactions (this helps reduce the risk that someone has comprised access to an account, including their two-factor authentication, and is trying to steal funds) or requiring approval for transactions from multiple email addresses (e.g., both a primary and secondary email address) or from multiple individuals (e.g., a requirement that 2-of-3 or 3-of-5 co-signers sign off on a transaction).
While both of these approaches may decrease the risk of stolen funds through a compromised account holder’s login (since now a hacker would need to compromise multiple individuals' accounts with potentially unknown identities), they still don’t address the concern of compromised funds at the exchange level.






Nerd Note:
Those familiar with the history of Coinbase’s “Vault” may recall that Coinbase actually used to have a vault service that did address the risk of compromise at the exchange level. This service was shut down in 2018 due to difficulties in managing Bitcoin forks and a reported lack of consumer demand, but it was a conceptually interesting offering to give greater confidence to those wanting to store funds on an exchange.
With this old version of Coinbase’s vault, three keys would be generated. Two of these three keys would be needed to move the funds. Coinbase controlled one key, the account holder controlled another key, and a third key was shared by Coinbase and the account holder, but encrypted with a password created by the account holder.
So, in practice, this meant that if someone lost their keys, then the account could still be recovered via both their password and Coinbase’s key. This provided extra peace of mind for those who may have been worried about making a mistake while implementing cold storage. At the same time, since Coinbase only possessed one of three keys in an unencrypted format, even if Coinbase was compromised (similar to how Mt. Gox was), then the stolen key would be useless to a hacker and the account holder could still access their funds using their keys.
This multi-key approach is referred to as “multisig”. Although multisig can still be implemented via other means, it is no longer directly supported by Coinbase. It should be noted that additional complications can arise when using multisig with respect to claiming “forks” (i.e., radical changes in a cryptocurrency protocol that results in generating a new version of that cryptocurrency, such as the hard fork that occurred with the creation of Bitcoin Cash). While Coinbase’s current Vault service can still require authorization from multiple co-signers, this is different from ‘true’ multisig, in the sense that the keys themselves are distributed to multiple parties or even just that there is redundancy in keys that belong to a single individual.
How Should Individuals Store Personally-Owned Crypto?
Ultimately, because an ideal solution is going to depend on the technical sophistication of a given user, there is no single ‘ideal’ storage solution that can be suggested.
That said, there are some general principles, and minimal thresholds of security, that should be considered when deciding how to store personally-owned cryptocurrency.
Least Tech Savvy: Reputable Exchange Or Storage-As-A-Service Solutions
For users with the lowest levels of tech savviness, storing through a reputable exchange or other reputable storage provider is worth considering.
While the “not your keys, not your coins” problem persists with storage on an exchange, the risk of storing funds with a major exchange like Coinbase is lower today than it was 5 years ago. However, users should still consider features such as those within Coinbase’s (new) “Vault” to add an additional level of security, and these features do need to be opted into by users.
It is important to note that, for security reasons, Coinbase’s Vault cannot be overridden – even by Coinbase. Users of the Vault features are going to have to wait 48 hours to move funds, which means possibly waiting 48 hours to liquidate an account, so they should understand this cannot be sped up, even when prices rise and fall significantly before a transaction can be executed.
Another related option worth considering is companies that specialize in cryptocurrency storage. For instance, BitGo offers a number of cold and hot storage options (including multisig capability, which facilitates the use of a multi-key requirement for money transactions, among other features) for higher net worth clients with at least $1 million USD to meet their new-account minimum. BitGo also maintains a $100 million insurance policy to protect user funds.
With time, the number of reputable firms within this space will certainly increase.
Additionally, advisor-specific solutions (e.g., Onramp Invest, led by CEO Tyrone Ross) are starting to appear with the aim of helping advisors, specifically, help their clients securely invest in cryptocurrency.
More Tech Savvy: Hardware Wallets
For individuals with a bit more tech savviness and the willingness to put some effort into securing their own cryptocurrency, reputable hardware wallets are likely a good middle ground for securing cryptocurrency without the hassle of managing paper wallets. Some of the major hardware wallet providers include Trezor, KeepKey, and Ledger.
Currently, Antonopoulus notes that there are four key common industry standards that have been developed around Bitcoin wallets. Each of the features listed here are discussed in more detail below.
- BIP-32 – Relates to the use of Hierarchical Deterministic (HD) wallets
- BIP-39 – Relates to the use of mnemonic code words
- BIP-43 – Relates to the use of multi-purpose HD wallet structures
- BIP-44 – Relates to the use of multi-currency and multi-account wallets
Wallets such as the Trezor Model T are compatible with these standards, which means that the mnemonic code (more on that later) used to back up a Trezor Model T could also be used to recover all transactions, keys, and addresses into another hardware wallet that is also compatible (e.g., Ledger Nano X).
To understand the importance of these standards, it is helpful to first distinguish between a deterministic and a non-deterministic wallet. A non-deterministic wallet is essentially one that generates keys that are not related to one another. These wallets are “just a bunch of keys” (JBOK), and not ideal for secure, user-friendly storage, since you have no way to recreate your wallet in the event that it is lost or stolen.
A deterministic wallet means that keys are related to one another and are generated from a single origin “seed.” You can think of a seed as the starting point of a branch to which anything that happens in the future could be traced back to. Hierarchical Deterministic (HD) wallets (see BIP-32 above) follow a certain structure in how keys are derived from the original seed to make this possible.
Further, these origin “seeds” that generate related keys are important because they can be backed up with mnemonic code words (see BIP-39 above), which provide an easier way for users to record their seed without errors.
As Antonopoulos notes, the following seeds are equivalent to one another:
- 0C1E24E5917779D297E14D45F14E1A1A
- army van defense carry jealous true garbage claim echo media make crunch






Nerd Note:
24-word mnemonic phrases are more secure than the 12-word phrase above, but the shorter phrase is included here simply for illustration purposes.
While both of the above are equivalent, the latter has an obvious advantage in being easier for humans to record (and possibly even memorize) and use without errors.
Thus, while BIP-32 relates to the ability of a wallet that allows the owner to trace activity back to the origin seed, BIP-39 relates to the ability of a wallet that allows its seed information to be recorded more easily. The technical details regarding the operation of mnemonic seeds is beyond the scope of this post, but the key point is that an entire wallet can be secured with a phrase (a long sequence of words) similar to the one above. So, if a hardware wallet is destroyed, lost, stolen, etc., a backup of this mnemonic phrase is all that is needed to ensure the Bitcoin is still secure.
Furthermore, hardware wallets come with all sorts of security features that ensure that someone merely possessing a hardware wallet will not be in a position to actually compromise the funds. And because hardware wallets operate as standalone devices (i.e., they aren’t computers that also need all sorts of unrelated software), they are not vulnerable to the same types of attacks that could easily compromise a computer (again, it’s best to assume that any computer ever connected to the internet has been compromised if it could be the waypoint to steal a large amount of cryptocurrency).
Some of the additional risks that hardware wallets can be safeguarded against include the following:
- Brute forcing a hardware wallet PIN. This involves repeated attempts to enter a PIN rapidly until one is found;
- Reflashing firmware on a hardware wallet. The original firmware of the wallet itself has been tampered with and swapped out for some malicious firmware;
- Computer theft. Since wallets are not tied to a particular computer, they are not compromised by theft or loss of the owner's computer;
- Hacking of the hardware wallet’s third-party servers. There is no need for users to rely on the servers of the company that manufactures the wallet;
- Shutdown of the company developing a hardware wallet. (i.e., everything still works or can be transferred to a different wallet even in the event that the company that manufactures Trezors gets shut down)
- Running a wallet recovery process on a compromised computer (i.e., even if you have to run a recovery process on a compromised computer, that does not pose a risk to one’s security)
The Trezor website includes a more detailed discussion of the risks outlined above.
Hardware wallets, such as the Trezor Model T, can also support the use of features such as splitting recovery seeds (i.e., splitting the recovery seed up into as many as 16 lists and defining some number of lists from 1 to 16 as what is required for a successful recovery) and multisig (a multi-key requirement for money transactions; see above). Multisig using hardware wallets will generally require the use of a software wallet that supports multisig (e.g., Electrum).
For a practical business use case, you could envision a CEO, CFO, and Board Member each being part of a 2-of-3 multisig arrangement with keys managed by hardware wallets. Such an arrangement would require at least two of the three individuals required to present their assigned key to authorize any transfers of money, providing protection against a single rogue actor misappropriating the funds while also building in redundancy in the event that one of the hardware wallets was lost, stolen, etc. and the mnemonic recovery code was also lost or improperly recorded.
All in all, hardware wallets provide a very high level of security via an interface that is fairly easy to use for someone with moderate technical sophistication and deserve consideration for individuals who want to securely store a significant amount of cryptocurrency without the added complexities of cold storage.
Most Tech Savvy (But Not Recommended): Paper Wallets
Ironically, storing cryptocurrency on old-fashioned paper (or similar media) may actually be the approach that demands the greatest level of tech savvy, but also promises—at least in theory—the greatest level of security. That said, paper wallets, which are simply physically printed private keys, are generally not advisable due to the technical savvy they take to truly pull off, plus the potentially large number of ways that users can easily make mistakes when dealing with paper wallets.
Of course, it’s not literally the storage on paper that is demanding from a tech savviness perspective. Rather, it’s ensuring that (a) keys are properly generated in a secure environment, and (b) ensuring that keys are preserved in a manner that allows them to be securely retrieved in the future.
First, there’s the challenge of trying to actually obtain a truly “air gapped” environment to produce keys, meaning that both the computer and any other devices used in the process (printing, transferring software, etc.) have never been online and are fully secure.
Then there’s the challenge of just properly carrying out the process of creating public and private keys.
But even after that’s complete, there are also additional challenges associated with failure to understand how Bitcoin transactions work, as the actual operations of transactions within the blockchain are often not intuitive (see further discussion from Andreas Antonopoulos in this video).
Example 1: Let’s assume that John created a paper wallet for himself by flipping a coin 256 times, where Heads = 1 and Tails = 0, and writing down the resulting 256-bit binary number that will serve as his private key.
John then follows the process below (described earlier in this article) in an entirely secure environment to generate a public address that can receive Bitcoin:
- Converts the binary number to hexadecimal;
- Determines the public key with elliptic curve multiplication; and
- Runs that public key through a hashing function to produce the public Bitcoin address.
At this point, John can now send funds to his newly created public key. To do this, John could go to Coinbase (or any other exchange), buy 3 Bitcoin (BTC), and then use his Coinbase wallet to send his 3 BTC to his newly created paper wallet. (Note: Transaction costs are ignored in these examples for simplicity’s sake.)
While the funds initially are at Coinbase and are not in a paper wallet, once they are sent to John’s paper wallet, then they are being securely stored in his paper wallet.
So long as John’s Bitcoin remains in his paper wallet and he’s extra careful not to lose his private key, his Bitcoin remains quite secure. In fact, in many respects, this process may be even more secure than using a hardware wallet.
However, let’s see what can easily go wrong if John doesn’t understand how transactions work.
Example 2: Suppose John now wants to buy something for 0.5 BTC.
Since he can’t initiate a transaction with just a paper wallet (it is, after all, just a piece of paper), he’s going to need to use a software wallet to initiate the transaction. John imports his private key to his software wallet.
He sends the 0.5 BTC from his paper wallet to the address requesting payment and completes his transaction, which leaves him with a balance of 2.5 BTC in his paper wallet (again, ignoring any transaction costs for simplicity’s sake). Not anticipating any need to make transactions again soon, John decides to delete his software wallet.
Now suppose some time passes and John wants to cash out the 2.5 BTC in his paper wallet. He again opens up a software wallet and tries to import his paper wallet’s private key. However, upon doing so, John discovers there is no BTC in his paper wallet!
In the example above, there are actually two crucial ways in which John might have erred.
The less intuitive error is that transactions in the Bitcoin network don’t work the way that people often intuitively think they will. When you send Bitcoin from one address to another, all “Unspent Transaction Outputs” (UTXOs) have to be “spent.”
In John’s case, the total UTXOs within his single address paper wallet was 3 BTC. That means that all 3 BTC needs to be spent on a transaction. 0.5 of the BTC will be sent to the vendor requesting payment, but then the 2.5 BTC in “change” (akin to when you spend $1 on something that only costs $0.80 and the two dimes you receive back are $0.20 of "change") also needs to be directed to an address. Many software wallets will default to sending all change to a “change address” – which is a new address generated by the software wallet – but many novice users of software wallets don’t realize this is happening in the background.
Therefore, in John’s case, unless he properly specified that he wanted the “change” to go back to his paper wallet, he could easily end up thinking the additional 2.5 BTC was on his paper wallet when he had really received the 2.5 BTC of "change" to his software wallet (that he subsequently deleted because he didn't realize that's where the "change" was deposited).
However, even if John had specified his paper wallet as the change address, this itself would likely be an error, since he had to input his private key in order to initiate the transaction and his wallet is no longer “cold” (i.e., never exposed to the internet). A much better approach would have been for John to generate a new paper wallet in a secure environment that would be specified as the change wallet for his transaction. (Which in turn means every time John engages in a new transaction he has to go through the process all over again in formulating a new paper wallet!)
The key point here is that most of this is not intuitive to Bitcoin novices. You really have to know what you are doing to use paper wallets in a safe manner, and even then, the marginal improvements in security are generally not worth the increased risks introduced due to technical complexity.
None of this is an issue with a quality hardware wallet, because it is all happening automatically in the background. This background sophistication (and error avoidance) is why hardware wallets are likely superior for almost all users. Furthermore, this is without considering multisig, mnemonic seed backup, and other potential benefits that can be achieved using a hardware wallet.
So, in short, paper wallets are not a good solution for any but perhaps the most hard-core cryptocurrency investors that hold very large amounts of Bitcoin or other cryptocurrencies where they are especially concerned about storing in the most secure manner possible (and are willing and ready to tackle the hassles and technical challenges).
In the end, those investing in cryptocurrency need to consider the unique challenges of securely storing personally owned cryptocurrency. Furthermore, users need to consider what solutions may work best for them, given their own technical sophistication.
For the least sophisticated users, letting a reputable exchange or a company that provides cryptocurrency storage as a service handle one’s keys may be the best route, despite the non-trivial risks associated with doing so. However, if taking this approach, investors should also consider enhanced security features (e.g., Coinbase’s Vault) that can further secure their funds.
For those who are a bit more tech savvy, a hardware wallet that meets current industry standards (e.g., Trezor, KeepKey, Ledger) may provide a good option for securely storing funds. Additionally, this security can be further enhanced through the use of software wallets that provide multisig and other capabilities (e.g., Electrum).
And although paper wallets may have some allure as providing the highest level of security possible, the technical complexity of properly implementing and using paper wallets should deter all but the most sophisticated individuals away from this route, and even for those who can handle the technical complexity, the relative ease of using hardware wallets and minimal security sacrificed will mean that hardware wallets are still the superior choice for most users.